
Co-managed IT services combine internal and external IT resources in order to create a strategic partnership and close gaps in your technology.
Instead of choosing between the benefits of an in-house team and an outsourced specialist, you can get the best of both worlds under one package.
Here’s an introduction to co-managed IT services and how to tell if they’re right for your business.

With COVID-19, videoconferencing has become a daily routine for most businesses. Anyone who has had to work from home lately understands and appreciates the importance of communication through videoconferencing with their clients or teams, some companies even take it a step further to host social gatherings. After this pandemic, video conferencing has become a way of life for most businesses. Zoom is easy to set up, easy to operate, and provides free access to up to 100 users at a time. But there are several downsides regarding its security. The ease of use of Zoom makes “bomb” an opening in Zoom conferences, easy for troublemakers. Information-security experts say that the protection of Zoom has had several security holes.

In the first weeks and months of the COVID-19 pandemic, the World Health Organization (WHO) reported a dramatic fivefold increase in the number of cyber attacks directed at its staff. It also warned the public to beware of the rampant cyber attacks and phishing scams that attempt to take advantage of pandemic panic.
Many other businesses and organizations are facing the barrage of these increased attacks, but because of the necessity of remote work, they are confronting these cyber threats with weakened out-of-office cybersecurity measures.
So, as many businesses look to make remote work a more permanent solution, one of the most important things they need to do is to protect their digital systems, assets, and communications.

Due to COVID-19, many businesses have had to quickly transition their employees to remote operations.
Under normal circumstances, businesses would usually have set up explicit processes and policies before switching employees to at-home work. However, quickly changing health guidelines and lockdown measures left some businesses scrambling as many employees who were working as usual one day were quarantined at home the next.
 Forms are a very common business practice for many organization, both SMBs and Enterprises. Forms can facilitate collecting data, save time, reduce mistakes and helps in creating a systematic recording of information. The problem is that they are not easy to create and once the data is collected, it is not easy to analyze.
Forms are a very common business practice for many organization, both SMBs and Enterprises. Forms can facilitate collecting data, save time, reduce mistakes and helps in creating a systematic recording of information. The problem is that they are not easy to create and once the data is collected, it is not easy to analyze.
Office 365 Forms is an easy-to-use tool that helps businesses create surveys, quizzes and polls and see results as they become available.
You can create forms in minutes, send and collect data and use their built-in analytics to evaluate responses. Forms can be private (only internal users with an Office 365 account) or public. Once the form is crated, it can be embedded in your website or simply sent in an email with a link; it even gives you the option to generate a QR code. Forms are also mobile friendly, so they can be filled out from mobile devices as well.
Office 365 Forms also gives you the option to collaborate and share this form with colleagues so that they can also make changes to the forms or use them as templates.
What is your current I.T. provider doing to make your business better?
Talk to us today and see what we can do for you!
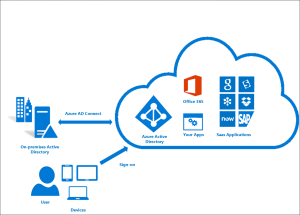 We all know Office 365 is the way to go for both SMBs and Enterprises, but deciding how to manage the users and accounting for the overhead it takes, are important things to consider. Organizations will usually have an on-premise Active Directory (server) with a list of all the users, first name, last name, usernames, and most important PASSWORD.
We all know Office 365 is the way to go for both SMBs and Enterprises, but deciding how to manage the users and accounting for the overhead it takes, are important things to consider. Organizations will usually have an on-premise Active Directory (server) with a list of all the users, first name, last name, usernames, and most important PASSWORD.
When you create a new Office 365 account (tenant), your out of the box option is to replicate the list of users you have on-premise to the cloud, you can do this by creating one by one or by importing a list. One of the biggest headaches we face as Network Administrators is the management of these accounts, if you make one change on-premise, you have to replicate the change in Office 365, not not mention the fact that sometimes the passwords can be different from on-premise (the password you use for your computer) and for Office 365, so now users have to remember 2 passwords instead of one.

5 Ways SMBs Can Save Money on Security
Small-to-medium sized businesses and large enterprises may seem worlds apart, but they face many of the same cyber-security threats. In fact, in recent years, cyber-criminals have increasingly targeted SMBs. This is because it’s widely known that SMBs have a smaller budget, and less in-house expertise, to devote to protection. Thankfully, there are several things SMBs can do today to get more from even the most limited security budget. And, no, we aren’t talking about cutting corners. Far too often, SMBs cut the wrong corners and it ends up costing them more money in the long run. It’s a matter of taking a smarter approach to security. Here are five smart approaches to take

Four Key Components of a Robust Security Plan Every SMB Must Know
Most businesses are now technology dependent. This means security concerns aren’t just worrisome to large corporate enterprises anymore, but also the neighborhood sandwich shop, the main street tax advisor, and the local non-profit. Regardless of size or type, practically any organization has valuable digital assets and data that should not be breached under any circumstances.
This makes it the responsibility of every business, especially those collecting and storing customer/client information, to implement a multipronged approach to safeguard such information.
Yes, we’re looking at you, Mr. Pizza Shop Owner who has our names, addresses, phone numbers, and credit card information stored to make future ordering easier and hassle free.

Just Because You’re Not a Big Target, Doesn’t Mean You’re Safe
Not too long ago, the New York Times’ website experienced a well-publicized attack, which raises the question – how can this happen to such a world-renowned corporation? If this can happen to the New York Times, what does this bode for the security of a small company’s website? What’s to stop someone from sending visitors of your site to an adult site or something equally offensive?
The short answer to that question is nothing. In the New York Times’ attack, the attackers changed the newspapers’ Domain Name System (DNS) records to send visitors to a Syrian website. The same type of thing can very well happen to your business website. For a clearer perspective, let’s get into the specifics of the attack and explain what DNS is.

Stay Secure My Friend… More Hackers Targeting SMBs
Many SMBs don’t realize it, but the path to some grand cybercrime score of a lifetime may go right through their backdoor. SMBs are commonly vendors, suppliers, or service providers who work with much larger enterprises. Unfortunately, they may be unaware that this makes them a prime target for hackers. Worse yet, this may be costing them new business.
Larger companies likely have their security game in check, making it difficult for hackers to crack their data. They have both the financial resources and staffing power to stay on top of security practices. But smaller firms continue to lag when it comes to security. In many cases, the gateway to accessing a large company’s info and data is through the smaller company working with them. Exposed vulnerabilities in security can lead cybercriminals right to the larger corporation they’ve been after.
Cybercriminals Target Companies with 250 or Fewer Employees
Research is continuing to show that cybercriminals are increasingly targeting smaller businesses with 250 or fewer employees. Attacks aimed at this demographic practically doubled from the previous year. This news has made larger enterprises particularly careful about whom they do business with. This means that any SMB targeting high-end B2B clientele, or those seeking partnerships with large public or government entities, must be prepared to accurately answer questions pertaining to security. This requires an honest assessment of the processes taken to limit security risks.
View Security Measures as Investments
CEOs must start viewing any extra investment to enhance security as a competitive differentiator in attracting new business. Adopting the kind of security measures that large enterprises seek from third-party partners they agree to work with will inevitably pay off. The payoff will come by way of new revenue-generating business contracts that will likely surpass whatever was spent to improve security.
Would-be business partners have likely already asked for specifics about protecting the integrity of their data. Some larger entities require that SMBs complete a questionnaire addressing their security concerns. This kind of documentation can be legally binding so it’s important that answers aren’t fudged just to land new business. If you can’t answer “yes” to any question about security, find out what it takes to address that particular security concern.
Where a Managed Service Provider Comes In
Anyone who isn’t yet working with a Managed Service Provider (MSP) should consider it. First, a manual network and security assessment offers a third-party perspective that will uncover any potential business-killing security risks. A good MSP will produce a branded risk report to help you gain the confidence of prospects to win new business.
A MSP can properly manage key elements of a small company’s security plan. This includes administrative controls like documentation, security awareness training, and audits as well as technical controls like antivirus software, firewalls, patches, and intrusion prevention. Good management alone can eliminate most security vulnerabilities and improve security.
Contact us at TheCompuLab